Problems with BLE
According to the new announcement for Bluetooth Low Energy 5, SIG believes that BLE 4.x has two main disadvantages:
- too short range,
- too low speed.
Not everyone agrees. Almost no one article (or speaker) makes the same point that these are really key issues for BLE. Instead, other problems are pointed to.
Here we introduce a few main issues with BLE based on our experience working with hardware companies to develop software and firmware.
Bluetooth Security
The Bluetooth Core Specification 4.2 (PDF, 24MB) provides quite good security that covers several security layers. The problem comes from the other side: appropriate implementation. Device manufacturers don’t seem to be serious enough about how they implement security features. Many manufacturers of wearable technology are keen to get their products to market as quickly as possible, with security sometimes tacked on as an afterthought. It’s important to highlight this key issue. Bluetooth v4.0 and v4.1 devices are insecure if the initial connection and pairing are sniffed (Bluetooth v4.2 is much more secure). Both devices must support LE Secure Connections to maintain security at this level. That’s why it’s often not difficult to identify that a certain BLE device was produced by a certain manufacturer. Why is this important?
Security case 1: Know who is who
It is well known that an easy way to know which BLE devices are near you is to use a program called “sniffer”. Image 1 shows the list of devices scanned by a sniffer. It’s easy to attribute a device to a particular person such as a celebrity, your CEO or the police officer leading an investigation against your company.
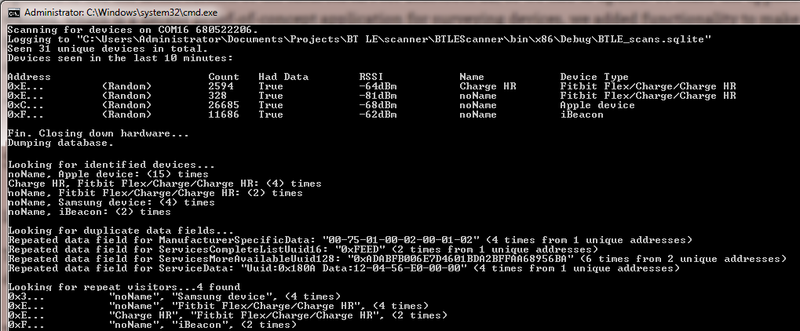
Image 1. The free Nordic sniffer lists all of the devices it can see. The same could be done with the help of free software for a common smartphone. [*]
Security case 2: Bluetooth wearable devices
BLE is widely used in wearable devices. Many of wearable devices contain very personal information about someone’s health and patterns of life. For wearable BLE module privacy may be the most important thing to keep secure.
Security case 3: Worries with mobile payments
BLE is suitable for making payments. Nevertheless, NFC is still more preferred than BLE, and remains the preferred technology for the in-store mobile payment transaction itself. The cause is in a distance. NFC work only near near 5 cm whereas BLE send signals to much longer distance. Potentially, BLE signal could be intercepted.
Security case 4: General hacking
There is fine practical research that show clearly how the traffic from BLEcould be intercepted. Packets can be intercepted and reassembled into connection streams. It is possible to make an attack against the key exchange protocol which renders the encryption useless against passive eavesdroppers. Also, sniffer could follow connections that have already been established at the time of sniffing.
Interaction in mesh
Number of devices that could interact each other grow each day. That is why highly important to have good ability to work in mesh network. BLE is typically point to point, point to multipoint. But still no clear information given, how many BLE-nodes could be in network with mesh topology without significant down set-up time and running a battery down. The hope is that a single BLE node can “talk” to several hundred nodes simultaneously as the theoretical limit is about 500 nodes. But it should be keep in mind that primary BLE was projected for low energy consumption. Bluetooth LE devices are aimed for lightning-quick connection, transmission of short bursts of tiny packets of data, followed by lightning-quick disconnection. In mesh network more connections will happen. The results are:
- quicker drain battery,
- longer setup time.
However, ZigBee is developed specially for Smart Home technology where mesh topology is common. And, 65,000 nodes that communicate each other is OK for ZigBee. Moreover, for ZigBee Smart Energy devices lower energy consumption is possible (but still no info which current or voltage these chips consume).
BLE Cost
Beacons based on BLE are a relatively new concept and still are not too cheap. BLE chips and beacons have range in price from $1 to $8 (by alibaba.com search info). This price is similar to ZigBee chip and modules range. But NFC and RFID tags have even less price. Individual tag generally costs between $0.10 and $0.60, depending on the specifications. Maybe comparing NFC tag and BLE beacon is slightly incorrect. But if somebody wish to apply BLE for mobile payments it should be cheap enough. In crowded stores, where a customer has never been before, large stores, or say, in public transport, NFC has the advantage over BLE because of cost and interoperability of the payment transactions reasons. Required investments for BLE payment transactions, compared to NFC, are higher at this moment in time.
Still less energy consumption needed
For the first sight, BLE is one of the most energy efficient technology in the world, comparing with other 802.15.4 realizations. According to Microsoft information dated by 1st April 2013, for all measured sleep intervals BLEachieved lower power consumption (10.1uA, at 120s interval), compared with ZigBee (15.7uA). But we should keep in mind that ZigBee has come out with the ZigBee Smart Energy specs that further reduce the power consumption. Also, we should not forget about alternative energy efficient technologies like Sigfox that adapted to work for tens years and applied in M2M industry.
Comparison of Internet of Things (IoT) Data Link Protocols
| Standart | ZigBee | Bluetooth LE | Z-Wave | NFC | Homeplug GP | Wi-Fi |
|---|---|---|---|---|---|---|
| IEEE Spec | 802.15.4 | 802.15.1 | ITU-T | ISO 13157 etc. | IEEE 1901-2010 | 802.11a/b/g |
| Freq, Band | 868/915 Mhz; 2.4 GHz | 2.4-2.5 Ghz | 908.42 Mhz | 13.56 MHz | 1.8 Mhz to 30 MHz | 2.4 GHz; 5 GHz |
| Max Signal Rate | 250 kb/s | 305 kbps | 40 kbit/s or 100 kbit/s | 424 kbit/s | ROBO: 4 Mbps to 10 Mbps; Adaptive Bit Loading: 20 Mbps to 200 Mbps | 54 Mb/s |
| Nominal Range | 10 m | ~50 m | ~30 m | ~5 cm | ~100 m | 100 m |
| Cryptography | AES block cipher (CTR, counternode) | AES Encryption | AES Encryption | Not with RFID | AES Encryption | RC4 stream cipher; (WEP), AES block cipher |
| Network type | WPAN | WPAN | WPAN | P2P | WPAN | WPAN/P2P |
| Spreading | DSSS | FHSS | FHSS | GSMA | BPSK, QPSK, 16 QAM, 64 QAM, 256 QAM, 1024 QAM | DSSS, CCK, OFDM |
| Modulation Time | BPSK (+ ASK), O-QPSL | TDMA | GFSK/ISM | ASK | OFDM | BPSK, QPSK, COFDM, CCK, MQAM |
| Coexistence mechanism | Dynamic freq. hopping | Adaptive freq. hopping | Adaptive freq. hopping | RFID | Dynamic freq. hopping | Dynamic freq. selection, transmit power control (802.1 1h) |
| Power Consumption | ~40 mA | ~12.5 mA | ~2.5 mA | ~50 mA | 0.5 W | ~116 mA (@ 1.8 V) |