The modern consumer’s digital ecosystem is more fragmented than ever. A typical household might contain smart speakers running different voice assistants, fitness trackers from various manufacturers, home automation devices using conflicting protocols, and entertainment systems spanning multiple platforms.
For businesses developing companion applications, this presents both an enormous opportunity and a complex technical challenge: how do you create a single, cohesive app that can seamlessly manage devices across different platforms and protocols?
In this post, we’ll outline a technical blueprint for overcoming this complexity, covering the critical architectural patterns and design choices that lead to success.
- The Complexity Behind Device Diversity
- The Core Architecture: A Universal Adapter for Your Devices
- Navigating Protocol Landscapes: Best Practices from the Field
- User Experience Design for Complex Systems
- Security Architecture: Trust in a Multi-Protocol World
- Performance Optimization: Managing Resource Constraints
- Testing Strategies for Complex Integrations
- Key Insights for Developing Unified Companion Apps
- The Future of Unified Device Management
- Developex: Your Partner in Companion App Development
- Final Thoughts,
The Complexity Behind Device Diversity
Before diving into solutions, it’s crucial to understand the roots of the challenge. Consumer devices operate across a bewildering array of technologies:
Communication Protocols: Bluetooth Low Energy (BLE), Wi-Fi Direct, Zigbee, Z-Wave, Thread, Matter, proprietary RF protocols, and cellular connections each have distinct characteristics, security models, and implementation requirements.
Data Formats: JSON, XML, binary formats, custom serialization schemes, and protocol buffers all serve different purposes and present unique parsing challenges.
Authentication Mechanisms: OAuth flows, certificate-based authentication, API keys, device pairing procedures, and biometric verification create a complex security landscape.
Platform Ecosystems: Apple HomeKit, Google Assistant, Amazon Alexa, Samsung SmartThings, and proprietary manufacturer ecosystems each impose their own development constraints and opportunities.
The challenge multiplies when you consider that these devices often exist in silos, designed primarily to work within their manufacturer’s ecosystem. Breaking down these silos while maintaining security, performance, and user experience requires sophisticated architectural thinking.
The Core Architecture: A Universal Adapter for Your Devices
Think of a universal travel adapter: it doesn’t matter what shape the power outlet is, you can still plug in your device. It has one familiar socket for your charger but multiple sets of prongs to fit any wall outlet in the world. The architecture of a great companion app works the exact same way, using a powerful software design principle called the Adapter Pattern.
Protocol Abstraction Layer
The goal is to create a Protocol Abstraction Layer. This is a single, consistent internal API that your application speaks, shielding it from the immense complexity of different communication methods. Underneath this unified layer, individual adapters do the messy work of translating your app’s simple commands into the specific, complex language each device protocol requires.
For example, fetching a temperature reading is wildly different for two common devices:
- A Bluetooth (BLE) fitness tracker might require connecting, discovering services via specific UUIDs, and reading binary data from a “characteristic.”
- A Wi-Fi smart thermostat likely uses a REST API, requiring an authenticated HTTP request to fetch a JSON response.
Without an abstraction layer, your app becomes a tangled mess of device-specific code. With one, both actions can be simplified to a single, clean command like device.getTemperature(). The correct adapter handles the complex BLE or HTTP communication behind the scenes, preserving each device’s unique features while hiding the complexity from your core logic.
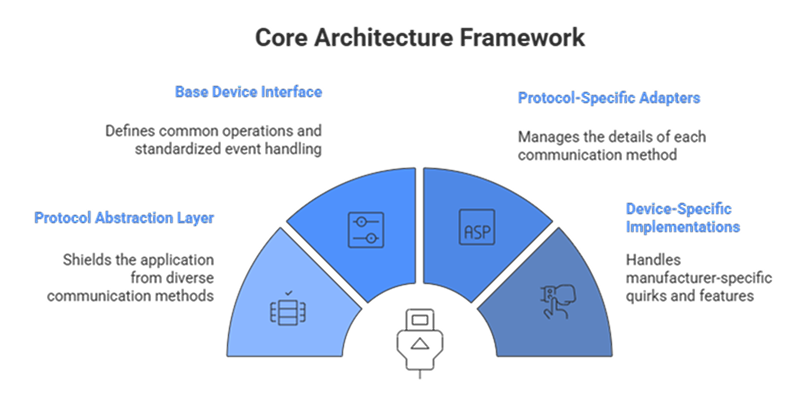
This is typically implemented through a hierarchical system of adapters:
Base Device Interface: Defines common operations like connect, disconnect, get status, and send command, along with standardized event handling for connection state changes and data updates.
Protocol-Specific Adapters: Handle the nitty-gritty details of each communication method. A Bluetooth adapter manages service discovery, characteristic mapping, and connection persistence, while an HTTP adapter handles authentication, request queuing, and error retry logic.
Device-Specific Implementations: Extend protocol adapters to handle manufacturer-specific quirks, custom data formats, and unique feature sets.
This architecture allows your application logic to remain protocol-agnostic while ensuring that device-specific optimizations and features remain accessible.
Command Translation and State Synchronization
One of the most challenging aspects of unified device management is handling command translation and state synchronization across devices with different capabilities and data models.
Imagine implementing a “bedtime mode” that should dim smart lights, lower the thermostat, lock smart doors, and pause entertainment systems. Each device category requires different commands, has different response patterns, and operates on different timescales. Smart lights might respond instantly, while a thermostat might take minutes to reach the target temperature.
Effective command translation requires building semantic maps between user intentions and device-specific actions. A successful command pipeline approach includes validation, translation, execution, and verification stages. This allows for sophisticated error handling and retry logic while maintaining clear audit trails for debugging.
State synchronization presents additional challenges, particularly when devices can be controlled through multiple interfaces. Your app might change a device setting, but the user might also adjust it directly on the device or through the manufacturer’s native app. Implementing conflict resolution strategies and maintaining eventual consistency across these control surfaces requires careful consideration of data flow patterns and user expectations.
Navigating Protocol Landscapes: Best Practices from the Field
With the Protocol Abstraction Layer established, your core application logic is protected from the messiness of device communication. However, the adapters themselves must be flawlessly executed. Different protocols present unique challenges related to connection reliability, data transfer efficiency, and security. Below, we dive into specific best practices for handling the most common communication technologies.
Bluetooth Low Energy: Managing Connection Complexity
BLE remains one of the most common protocols for consumer devices, but it’s also one of the most challenging to implement reliably. Connection management, service discovery, and data synchronization across different device manufacturers and operating system versions requires deep protocol knowledge.
Success BLE implementation requires:
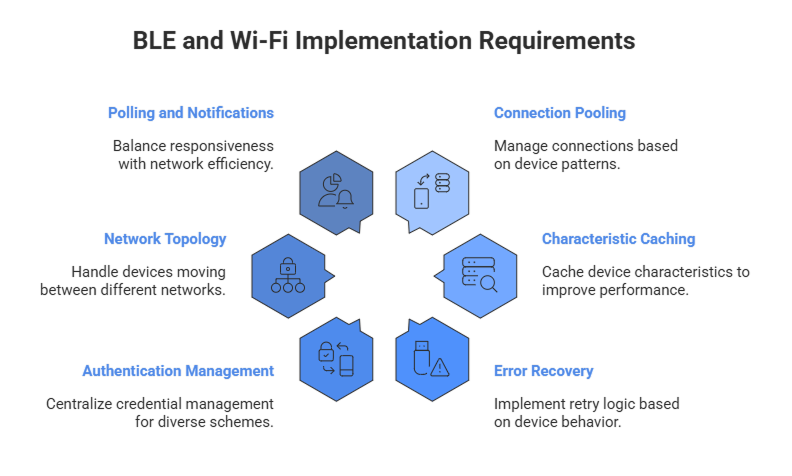
Connection Pooling and Management: Implement sophisticated connection pooling that considers device-specific connection patterns. Some devices perform better with persistent connections, while others benefit from connect-on-demand patterns to preserve battery life.
Characteristic Caching: Build intelligent caching layers for device characteristics and services. This improves performance and reduces the need for expensive service discovery operations, but requires careful invalidation logic to handle device firmware updates.
Error Recovery Strategies: Implement exponential backoff with jitter for connection attempts, but customize retry logic based on device behavior patterns. Some devices require specific delay patterns between connection attempts to avoid entering error states.
Wi-Fi and HTTP-Based Protocols: Scaling and Security
Wi-Fi connected devices often expose HTTP APIs, which might seem straightforward but present their own challenges at scale. Managing authentication across multiple devices, handling network topology changes, and implementing efficient polling strategies requires careful architectural planning.
Certificate and Authentication Management: Develop centralized credential management systems that can handle diverse authentication schemes while maintaining security best practices. This includes secure storage, automatic token refresh, and graceful handling of authentication failures.
Network Topology Awareness: Implement discovery mechanisms that can handle devices moving between networks, changing IP addresses, and operating behind different firewall configurations. mDNS and UPnP discovery can be effective, but require robust fallback mechanisms.
Efficient Polling and Push Notifications: Balance real-time responsiveness with network efficiency through adaptive polling strategies and WebSocket connections where supported. Implement intelligent batching for devices that support bulk operations.
Emerging Protocols: Matter and Thread
The Matter standard represents a significant step toward device interoperability, but adoption is still fragmented. When designing unified companion apps, it’s important to build architectures that can take advantage of Matter’s standardization while maintaining backward compatibility with existing device ecosystems.
Effective approach involves building Matter adapters alongside existing protocol implementations, allowing applications to gradually migrate devices to standardized interfaces as they become available. This requires careful API design to ensure that Matter-specific features can be exposed without breaking compatibility with legacy device implementations.
User Experience Design for Complex Systems
Creating intuitive user experiences for unified device management requires balancing comprehensive functionality with cognitive simplicity. Users shouldn’t need to understand the technical complexity of their device ecosystem, but they should have access to the full capabilities of their devices.
Progressive Disclosure and Contextual Interfaces
The most successful unified companion apps use progressive disclosure patterns that present simple, common operations prominently while making advanced features discoverable when needed. This might mean exposing a simple “turn on lights” button while hiding detailed scheduling, color temperature, and scene management behind contextual menus.
Contextual interfaces adapt based on device capabilities, user behavior patterns, and environmental factors. A lighting control interface might emphasize color features during evening hours while focusing on brightness during daytime use. Device grouping and scene management become more prominent as users add more devices to their ecosystem.
Cross-Device Interaction Patterns
Users increasingly expect their devices to work together intelligently. This requires implementing sophisticated interaction patterns that can coordinate actions across multiple devices while providing clear feedback about system state and operation progress.
Effective cross-device interactions require careful consideration of timing, dependency management, and error handling. If a “movie night” scene fails to execute on the sound system but succeeds on the lighting, users need clear feedback about the partial failure and options for remediation.
Security Architecture: Trust in a Multi-Protocol World
Security in unified companion apps is particularly challenging because you’re essentially creating a single point of access to multiple device ecosystems, each with their own security models and threat profiles. This requires implementing defense-in-depth strategies that protect both individual device communications and the overall system architecture.
Zero-Trust Device Communication
Implement zero-trust principles by treating every device communication as potentially compromised. This means:
End-to-End Encryption: Use device-specific encryption keys and avoid storing sensitive device credentials in centralized locations where possible. Implement key rotation strategies that can handle devices with different security capabilities.
Communication Validation: Validate all device communications through cryptographic signatures or certificates, and implement replay attack prevention through nonce-based systems.
Privilege Isolation: Limit each device adapter’s access to only the resources it specifically needs, and implement sandboxing strategies that prevent compromised device drivers from affecting other system components.
Privacy-Preserving Data Aggregation
Unified companion apps often aggregate sensitive data from multiple sources, creating privacy concerns that extend beyond individual device capabilities. Implement privacy-preserving aggregation techniques that allow for useful analytics and automation without exposing detailed user behavior patterns.
This might include local processing strategies that keep sensitive data on-device, differential privacy techniques for usage analytics, and user-controlled data retention policies that respect varying privacy preferences across different device categories.
Performance Optimization: Managing Resource Constraints
Mobile devices have limited resources, but unified companion apps must maintain connections and synchronization with potentially dozens of devices. This requires sophisticated resource management strategies that balance functionality with battery life and network usage.

Intelligent Connection Management
Implement adaptive connection strategies that consider device usage patterns, battery levels, and network conditions. Frequently used devices might maintain persistent connections, while occasionally accessed devices can use on-demand connection patterns.
Connection prioritization algorithms should consider user behavior patterns, device criticality (security devices might receive priority), and current system resource availability. Implement graceful degradation strategies that maintain core functionality even under resource constraints.
Data Synchronization Optimization
Develop synchronization strategies that minimize redundant data transfer while maintaining system responsiveness. This might include:
Delta Synchronization: Only transfer changed data rather than complete device states, particularly important for devices with large configuration profiles.
Predictive Prefetching: Use machine learning techniques to predict which device data will be needed and prefetch it during low-usage periods.
Compression and Batching: Implement intelligent compression and request batching that considers device capabilities and network conditions.
Testing Strategies for Complex Integrations
Testing unified companion apps requires sophisticated strategies that can validate functionality across multiple protocols, device types, and network conditions. Traditional unit testing approaches are insufficient for systems with complex hardware dependencies and real-time communication requirements.
Device Simulation and Emulation
Develop comprehensive device simulators that can replicate not just successful communication patterns, but also the various failure modes and edge cases that occur with real hardware. This includes simulating connection drops, authentication failures, firmware update scenarios, and network topology changes.
Effective device simulation requires understanding the timing characteristics and state management patterns of real devices. A Bluetooth device simulator should replicate the connection establishment delays and service discovery patterns of actual hardware, including manufacturer-specific quirks and limitations.
Integration Testing in Realistic Environments
Create testing environments that replicate real-world deployment scenarios, including multiple concurrent device connections, varying network conditions, and resource constraints. Use chaos engineering principles to validate system resilience under adverse conditions.
Implement automated testing pipelines that can validate cross-device interactions and scene execution across different device combinations. This becomes particularly important as the number of supported devices grows and manual testing becomes impractical.
Key Insights for Developing Unified Companion Apps
Our experience developing unified companion apps across various industries has revealed several critical insights that often aren’t apparent during initial development phases.
Graceful Degradation Strategies
Users expect unified companion apps to work even when individual devices are offline, experiencing connectivity issues, or undergoing firmware updates. Implement sophisticated fallback mechanisms that maintain core functionality while clearly communicating system limitations.
This might mean providing cached device states with clear timestamps, offering manual override options when automated systems fail, or implementing mesh communication patterns where supported devices can relay information about offline devices.
Firmware Update Management
Device firmware updates can break existing integrations, change API behaviors, or introduce new security requirements. Develop update detection and adaptation strategies that can handle these changes gracefully.
Implement version tracking and compatibility matrices that allow your application to adapt communication patterns based on detected firmware versions. Create rollback mechanisms for critical integrations that can revert to known-good communication patterns when new firmware versions cause issues.
Scalability Considerations
As users add more devices to their ecosystems, unified companion apps must scale gracefully without degrading performance or user experience. This requires careful architectural planning that considers both technical scalability and user interface complexity.
Implement device grouping and management hierarchies that allow users to organize large device collections logically. Create efficient batch operations that can manage multiple devices simultaneously without overwhelming system resources or network connections.
The Future of Unified Device Management
The world of consumer devices is always changing. To stay ahead, unified companion apps need to be designed to adapt and grow with it. Instead of just reacting to new technology, a strong architecture can anticipate it. This means creating a system that can handle new devices and protocols while still supporting older ones.
Artificial Intelligence for a Smarter Experience
Artificial intelligence is becoming essential for managing complex device ecosystems. AI can significantly improve user experience by making devices work for the user, not the other way around.
- Predictive Maintenance: AI can learn from device usage to predict potential issues before they happen.
- Usage Pattern Recognition: It can identify a user’s habits and suggest helpful automations, like adjusting lighting when they arrive home.
- Automated Scene Creation: AI can automatically create and suggest personalized scenes, reducing the burden of manual setup.
Edge Computing Opportunities
As edge computing capabilities improve, unified companion apps can leverage local processing power to reduce latency, improve privacy, and maintain functionality during network outages. This requires architectural flexibility that can distribute processing between mobile devices, local edge nodes, and cloud services based on current system capabilities and requirements.
Interoperability Standards Evolution
Continue monitoring the evolution of interoperability standards like Matter, Thread, and emerging protocols. Design system architectures that can take advantage of standardization opportunities while maintaining support for existing device ecosystems during transition periods.
Developex: Your Partner in Companion App Development
Companion apps have become a defining factor in how users experience modern devices. A seamless, reliable app can elevate a product from functional to essential – strengthening brand reputation and unlocking new revenue opportunities.
At Developex, we build cross-platform companion applications that connect devices into intuitive, future-ready ecosystems. Our expertise spans:
- Smart Home & IoT: Multi-device apps for lighting, HVAC, and security systems.
- Healthcare & Fitness: BLE-based apps for trackers, medical IoT, and connected wellness devices.
- Gaming & Audio Devices: Companion apps for RGB lighting, fan controllers, headsets, and audio processing.
- Cross-Platform Solutions: iOS, Android, desktop, and cloud integrations with unified UX.
What sets us apart:
- Deep knowledge of BLE, Wi-Fi, Matter, Zigbee, Z-Wave, Thread.
- Strong expertise in C++, Qt, mobile development, and firmware integration.
- Proven success in creating scalable, secure, and intuitive apps for global brands.
With Developex, companies gain a partner who ensures companion apps are not only technically sound, but also strategic drivers of product and brand success.
Final Thoughts,
The journey of building a unified companion app is a balance between managing the complexity of today’s fragmented device landscape and anticipating the opportunities of tomorrow. The core of a successful app isn’t just a list of features, but a robust architecture designed for abstraction, security, and scalability. By focusing on a universal adapter model, graceful degradation, and a forward-thinking approach to emerging technologies like AI and edge computing, you can build a truly resilient and user-friendly experience.
The challenge of creating a single app to manage an entire digital ecosystem can seem daunting, but with the right architectural blueprint, it’s an achievable goal that can unlock significant value for your business and your users.
Ready to build your next-generation companion app?
At Developex, we’ve spent years building, scaling, and maintaining complex companion applications for leading brands. Our experience is your advantage. Contact Developex to discuss how our expertise in unified device management can accelerate your development timeline and ensure market-leading results.